Writeup: Missing Tools

The challenge brief tells us that we have a severely broken Linux install with only a few commands available. We're told nothing about where the flag is, in fact nothing about the environment at all. Connecting to the provided IP and port, we see the string SSH-2.0-dropbear_2020.81 - this must be a an SSH server. We use the provided username and password, and we're in.
Linux restricted shell
$ ls
This command has been disabled by your administrator.
$ dir
This command has been disabled by your administrator.
$ cat /etc/passwd
This command has been disabled by your administrator.They weren't lying, huh. We don't even have tab suggestions. However, after a quick internet search for ways to view the directory listing without ls, we find we can use echo * as an ls substitute. Running that, we see a singular file in the directory called flag.txt. It looks like we'll have to print the contents of this, but without any obvious tools.
But what tools do we have? Recall that Linux knows where everything is from the PATH variable - and it looks like we can print that one out.
$ echo $PATH
/usr/bin:/bin
$ echo /usr/bin/* /bin/*
/usr/bin/cal /usr/bin/dirname /usr/bin/eject /usr/bin/file /usr/bin/lsof /usr/bin/mkpasswd /usr/bin/sha256sum /usr/bin/split /usr/bin/test /usr/bin/time /usr/bin/wc /usr/bin/whoami /usr/bin/yes /bin/[ /bin/bash /bin/cat /bin/date /bin/dir /bin/echo /bin/false /bin/grep /bin/head /bin/help /bin/less /bin/ls /bin/more /bin/pwd /bin/sh /bin/sleep /bin/sync /bin/tail /bin/toysh /bin/true /bin/vi /bin/vimWell, calendar isn't helpful. It looks like some of these commands have also been repurposed into displaying a simple forbidden message, and we can't use those (cat, grep, head, less, more, tail, vi, vim). Interestingly enough, we do have sha256sum. Let's run that on the flag:
$ sha256sum flag.txt
874b03af106fa42353eeff6d7be05f43ba8dcf3e1d8298cbd82bc0af6993c707 flag.txtBut brute-forcing that would be a massive pain, and not the right solution to the challenge. If only the flag was shorter, then we could crack the hashes more easily?
Split!
Split takes a file and writes multiple out files of the format x**, creating a new file whenever the previous one has reached the number of bytes you tell it. If we run split rather aggressively, by splitting every 3 bytes, we should end up with some hashes that are trivially reversible online.
$ split -b 3 flag.txt
$ echo *
flag.txt xaa xab xac xad xae xaf xag xah xai xaj xak xal
$ sha256sum xa*
df10b4bd068175bd33f200e48e721a019091c67c06c26ae273da5aaf51424618 xaa
582c3f2f5c5c630d0ee458d5d7c859e7ed36d6fb5862a761e110562438bd4272 xab
a7f5397443359ea76c50be82c77f1f893a060925b51a332cc5da906f83d3344e xac
569a659ae7633e5ddd7f523b283c1169dad3eb99a3da4b3ad2d5619d9236dc12 xad
7096489b19f4ab1b6c9e1502367c18d5e3adcfeb21b0a0282041ca99e798a14d xae
618630d1fed7f03ed43dfb03eeae681c1812177c43d3afe1cbe32bb3fee12bf9 xaf
f2f9ca19dad6782e5e92edd758439f11067ae23ab0d418a56f406de6c9bb151a xag
f481b98f744da847f44f5e67996010859061dca4945e87396016a1ef4ac38460 xah
de7bc3aee118c9689e2cba40c4c427ab8986b8a37c9c4f837e019559de9faffd xai
a14d511b5d8b444da7ea5ab52feb71271a46bb8374ab24f5251701b23bef4276 xaj
56fb98daea7879c3e2218eb960b9150c2d7978686af5f7f43f80641a6f62b22a xak
df8238034568781a5df3098ed46435fee0df6c807938e7dbeccb0a29f887d246 xalIn a proper shell, we can post process:
➜ ~ $ cat out
df10b4bd068175bd33f200e48e721a019091c67c06c26ae273da5aaf51424618 xaa
582c3f2f5c5c630d0ee458d5d7c859e7ed36d6fb5862a761e110562438bd4272 xab
a7f5397443359ea76c50be82c77f1f893a060925b51a332cc5da906f83d3344e xac
569a659ae7633e5ddd7f523b283c1169dad3eb99a3da4b3ad2d5619d9236dc12 xad
7096489b19f4ab1b6c9e1502367c18d5e3adcfeb21b0a0282041ca99e798a14d xae
618630d1fed7f03ed43dfb03eeae681c1812177c43d3afe1cbe32bb3fee12bf9 xaf
f2f9ca19dad6782e5e92edd758439f11067ae23ab0d418a56f406de6c9bb151a xag
f481b98f744da847f44f5e67996010859061dca4945e87396016a1ef4ac38460 xah
de7bc3aee118c9689e2cba40c4c427ab8986b8a37c9c4f837e019559de9faffd xai
a14d511b5d8b444da7ea5ab52feb71271a46bb8374ab24f5251701b23bef4276 xaj
56fb98daea7879c3e2218eb960b9150c2d7978686af5f7f43f80641a6f62b22a xak
df8238034568781a5df3098ed46435fee0df6c807938e7dbeccb0a29f887d246 xal
➜ ~ $ cat out | cut -f 1 -d ' '
df10b4bd068175bd33f200e48e721a019091c67c06c26ae273da5aaf51424618
582c3f2f5c5c630d0ee458d5d7c859e7ed36d6fb5862a761e110562438bd4272
a7f5397443359ea76c50be82c77f1f893a060925b51a332cc5da906f83d3344e
569a659ae7633e5ddd7f523b283c1169dad3eb99a3da4b3ad2d5619d9236dc12
7096489b19f4ab1b6c9e1502367c18d5e3adcfeb21b0a0282041ca99e798a14d
618630d1fed7f03ed43dfb03eeae681c1812177c43d3afe1cbe32bb3fee12bf9
f2f9ca19dad6782e5e92edd758439f11067ae23ab0d418a56f406de6c9bb151a
f481b98f744da847f44f5e67996010859061dca4945e87396016a1ef4ac38460
de7bc3aee118c9689e2cba40c4c427ab8986b8a37c9c4f837e019559de9faffd
a14d511b5d8b444da7ea5ab52feb71271a46bb8374ab24f5251701b23bef4276
56fb98daea7879c3e2218eb960b9150c2d7978686af5f7f43f80641a6f62b22a
df8238034568781a5df3098ed46435fee0df6c807938e7dbeccb0a29f887d246And paste into CrackStation.
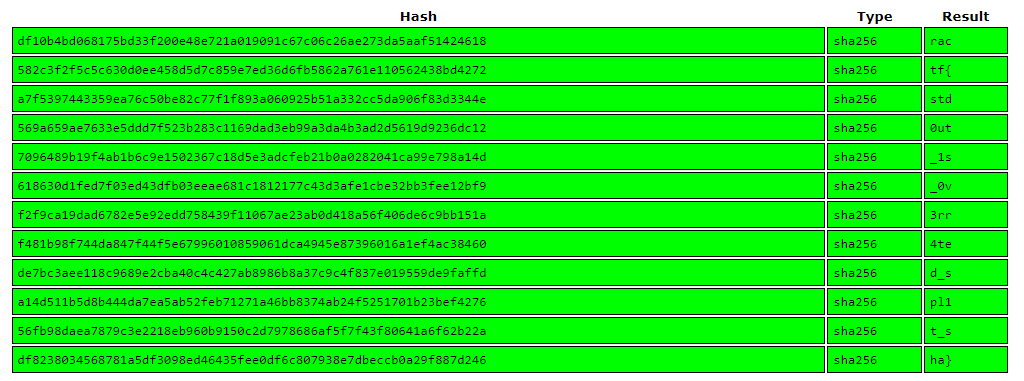
Piecing together the results, we can retrieve the flag as ractf{std0ut_1s_0v3rr4ted_spl1t_sha}. That was painful.
