Writeup: RSFPWS: Invulnerable

Welcome to my write-up of my challenge from RACTF 2021, RSFPWS: Invulnerable. We'll be solving this challenge today with Cheat Engine (be careful if you download it to follow along; the installer has some boxes ticked by default which probably shouldn't be).
The challenge we're presented with is a Unity game which connects to a server. Presumably, going by the challenge name, we need to make ourselves invulnerable. In this writeup we're going to do this via memory editing of instructions.
Let's first start by downloading the client and connecting to the server. We're presented with the following two boxes:
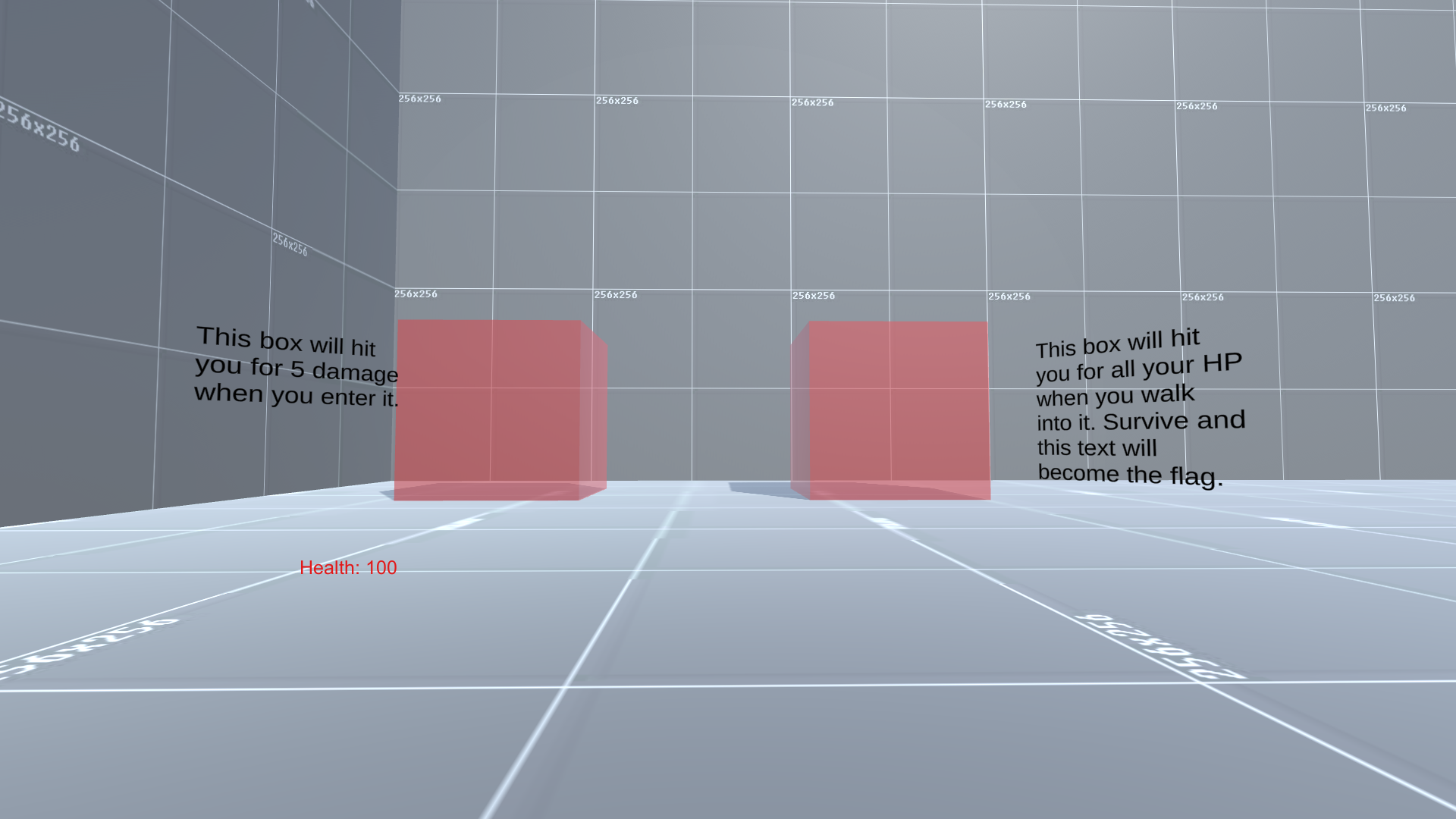
Clearly we need to figure out some way to stop the box on the right from writing to our HP value. Let's head over to cheat engine, attach to the process, and see if we can't find our Health variable. We start an exact value scan for the value 100 (We can see this in the UI), then incrementally scan for 95, 90, 85, etc. as we decrease our health by walking into the left box:
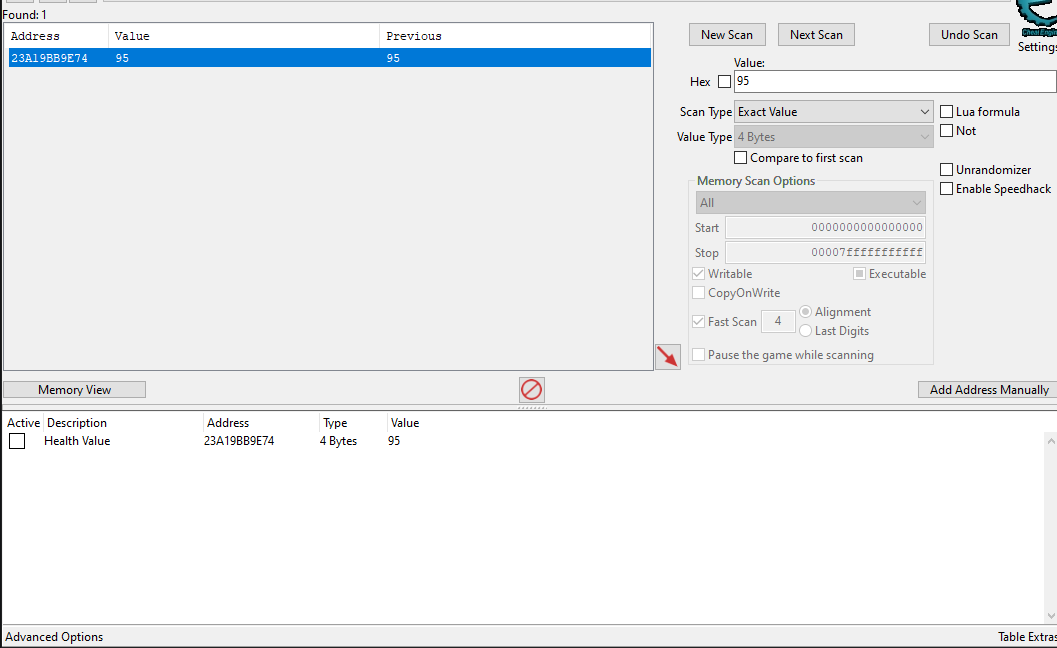
Double click the value to add it to the address list.
Let's attach the Cheat Engine debugger to this process and see what writes to the address. Hit F6 on the address to attach the debugger and instruct it to find which instructions write to that address. Let's enter the right box and see what gets written.
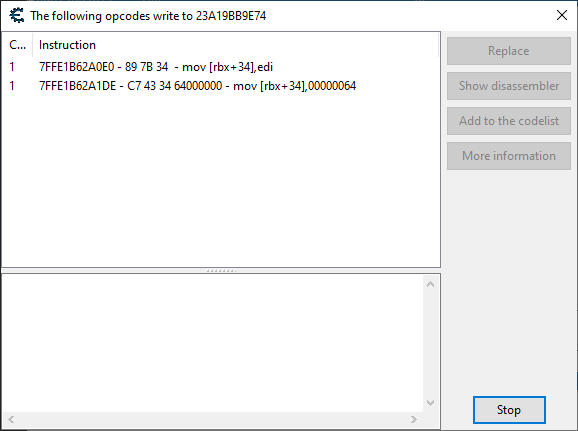
As we can see, the debugger captures the instructions which modify the value. Out of the two, the one we most probably want is mov [rbx + 34], edi, since mov [rbx + 34], 064 looks like it just resets our health too 100 (0x64). Click the instruction, then "Show disassembler" to open it in the memory view.
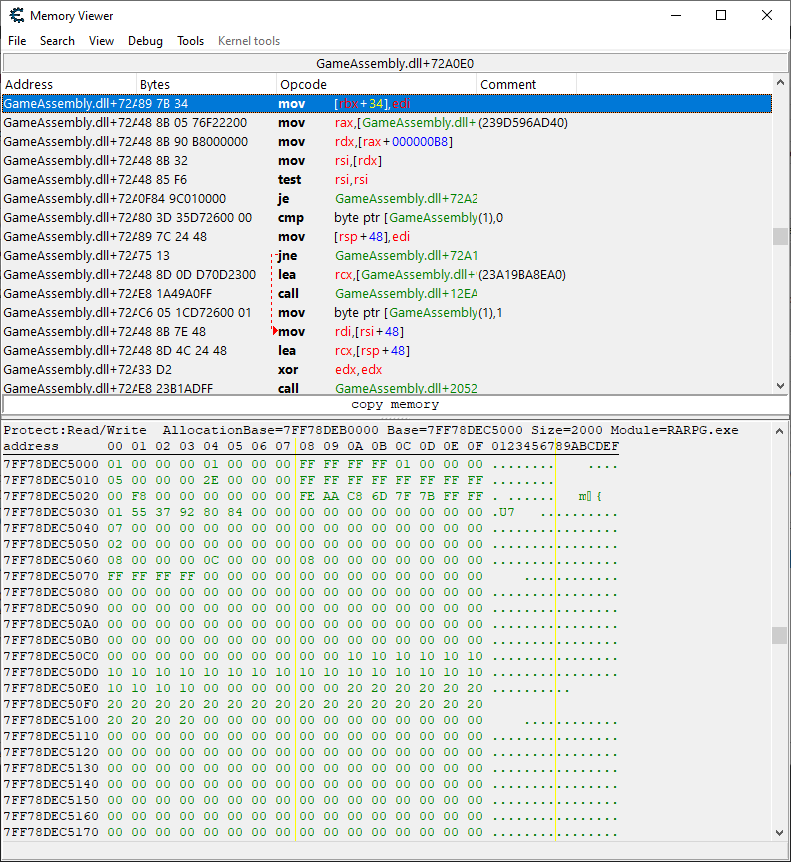
From hear you can replace the instruction with nops, and you've solved the challenge. Simply walk into the red box and receive the flag.
